IoT Security
The Internet of Things, or IoT, is a pivotal component of the future and is driving initiatives from Smart Cities through Ubiquitous Computing and Augmented Reality. Of course the next step up from Smart Cities is a Smarter Planet. But we aren’t at Smart Cities yet.
An enabling technology like IoT can also have roadblocks to adoption. The principal ones being addressed now are:
- power consumption
- cost of goods
- size
- security
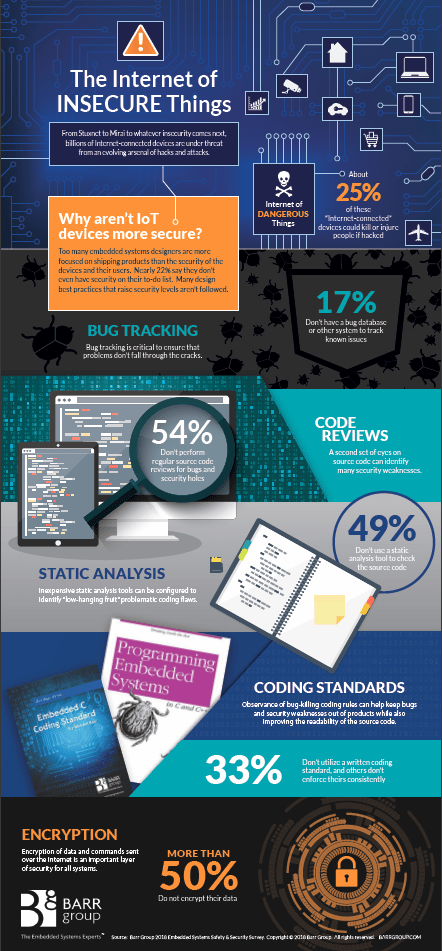
The biggest issue right now is IoT Security. Recent DDoS (Distributed Denial of Service) attacks have used IoT Devices as the attack launchers. They are being selected because many have weaker security than fully fledged computing devices.

DDoS or Distributed Denial of Service
In a recent article on IEEE Spectrum on the Path to IoT Security it is argued that IoT Manufacturers must take responsibility and not leave it up to end users. There is also a role of industry standards however no clear set of standards have yet been agreed. So although 2016 is the Year of IoT, with this being the single biggest category of product shipped, it is still very early days where things like IoT Security and IoT Interoperability are concerned.
IoT Security versus Software Security
This is not a new dilemma. Software Security is always important and it becomes increasingly important as Internet Communicating IoT Devices become more widespread. One apparent assumption underlying all this is that an IoT Device must be a fully IP Stack capable platform. That is not necessarily the case. In the video I shared about our Water Metering Remote Telemetry project one thing I didn’t mention is that the data stream is all driven from the IoT Device. There is nothing to log into. You can’t patch it with a Windows, Linux or other OS patch to override its function. It is not capable of being used in a DDoS attack because you can’t get to anything in it that can do that. So it is inherently secure against that form of risk.
Internet of Things Connectivity
However there are other risks. Nick Hunn has an insightful piece on Wireless Security for IoT where he argues that we are declaring security is present while having no evidence of proving it. That article is a little dated but the basic tenets still seem to apply. Just because a manufacturer or industry alliance states they have addressed security, it doesn’t make it automatically true.
So IoT Security is Software Security with the added component of protecting the physical hardware.
IoT Security in the Future
We still don’t have standards, so for now, individual device manufacturers and alliance members will need to ensure they have adequate security out of the box. The level of security required is determined by the importance of the data, either its security against unauthorised access, or its integrity against falsification. And at the asset level, its proof against either being disabled or used as an attack vector.
As an example, I am personally not so concerned if a hacker can find out how much electricity use my smart meter is reporting. Unless they get time of day usage and can correlate with other data sources to work out in advance when we aren’t home so they can rob us. My energy provider probably cares more about this data for all its customers coming into a competitors hands. Or maybe not. But I do care that I don’t get an outrageous bill because they were able to send fake data for my account to a server.
And energy grid managers care about usage data and Smart Meter appliance management being used to crash an entire electricity grid!
In the case of the Water Metering Remote Telemetry project I care that it remains online and working because otherwise someone will have to travel a long way to fix it. We have a facility in Gilgandra that is 892Km away as the crow flies. It will take a full day to get there and then another to get back again. So I want it to be proof against some hacker disabling its communication ability. Since it has a physical antenna, I do care about that being hard to break. So some of these devices are put above normal reach and everything is inside a secure plastic case including the antenna. And our customer wants to know the reported water usage is correct. This means no missing data, and no incorrect data. They use the data to bill their customers.
One simple way to mess up data is a Replay Attack. If you can intercept and copy a data transmission, then you can play back that transmission any time you want to. You don’t even have to understand the content, the encryption, anything. Simply capture a HTTP POST or GET and replay it. Why does this matter? Because if the data transmitted is the volume of water used since the last report, then every time you play it back, you add to someone’s water bill. Or you distort the level of water the system believes is in a tank or reservoir. You can protect against these attacks in a number of ways but you have to consider the need to protect against them first of all.
There is a large volume of material on this topic. Here are some additional articles you might find useful for broadening your perspective on this topic:
I’m sure you won’t find it hard to search out a lot more articles. Just consider this. Once it has an Internet connection, any device can access anywhere in the world. And most firewalls protect against incoming attacks. A corrupted device on the inside can get out any time it wants to.

Internet of Things Global Reach
And if you want a really interesting view of what this could be like 10 years from now, I recommend reading Rainbow’s End by Vernor Vinge. Enjoy. And this isn’t my first reference to this book because I think it is fairly prescient in its exploration of a most probable future.
Successful Endeavours specialise in Electronics Design and Embedded Software Development, focusing on products that are intended to be Made In Australia. Ray Keefe has developed market leading electronics products in Australia for more than 30 years. This post is Copyright © 2016 Successful Endeavours Pty Ltd.